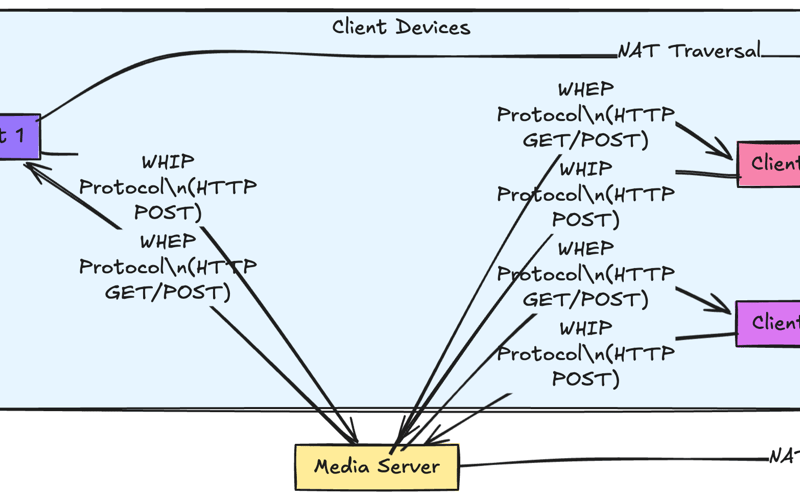
14
Nov
In networking, efficient and fair use of shared communication channels is critical to minimizing data collisions and maximizing network performance. Two foundational protocols that manage network access in this context are Carrier Sense Multiple Access with Collision Detection (CSMA/CD) and Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). These protocols are essential to network performance, particularly in Ethernet (for CSMA/CD) and wireless (for CSMA/CA) environments. Let’s dive into the details of how each protocol works, where it’s used, and its significance in network management. What is CSMA? Carrier Sense Multiple Access (CSMA) is the overarching method that allows devices on…