16
Nov
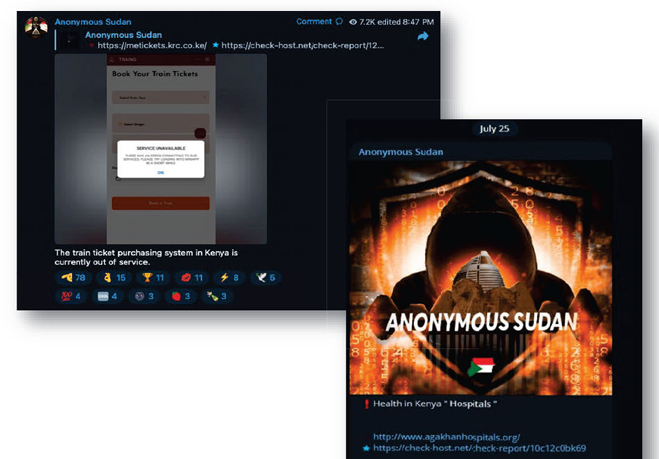
Back in October, the FBI and Cybersecurity and Infrastructure Security Agency (CISA) admitted that they were looking into "the unauthorized access to commercial telecommunications infrastructure by actors affiliated with the People’s Republic of China." These bad actors, collectively called "Salt Typhoon," allegedly targeted US officials and staffers for the recently concluded presidential elections. A few days later, though, The Wall Street Journal reported that the group had access to a lot more people than originally thought. Basically, the hackers could have accessed the data of any American who's a customer of AT&T and Verizon. That list of carriers has grown…