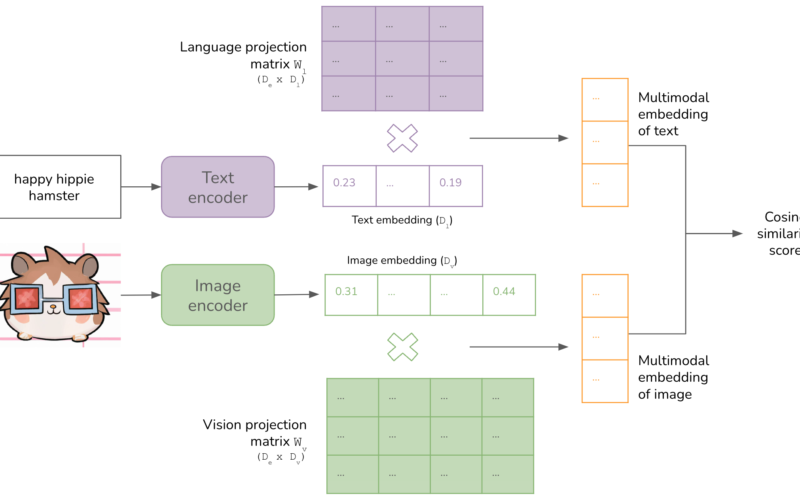
14
Oct
Hello again, and welcome to today's tutorial. Today, we are going to build a simple password strength checker using Python. We’ll explain how the code works step-by-step and give tips on how to improve your passwords. Why is Password Strength Important? A weak password makes it easier for hackers to guess or crack using various methods, putting your personal information at risk. A strong password is: Long enough (at least 12 characters) Uses a mix of letters (both uppercase and lowercase), numbers, and special characters Avoids common or predictable words Let’s get started by building a tool that assesses the…